Law enforcement and judicial authorities worldwide have disrupted one of the most significant botnets of the past decade: EMOTET. Investigators have now taken control of its infrastructure in an international coordinated action.
This operation is the result of a collaborative effort between authorities in the Netherlands, Germany, the US, the UK, France, Lithuania, Canada and Ukraine, with international activity coordinated by Europol and Eurojust. This operation was carried out in the framework of the European Multidisciplinary Platform Against Criminal Threats (EMPACT).
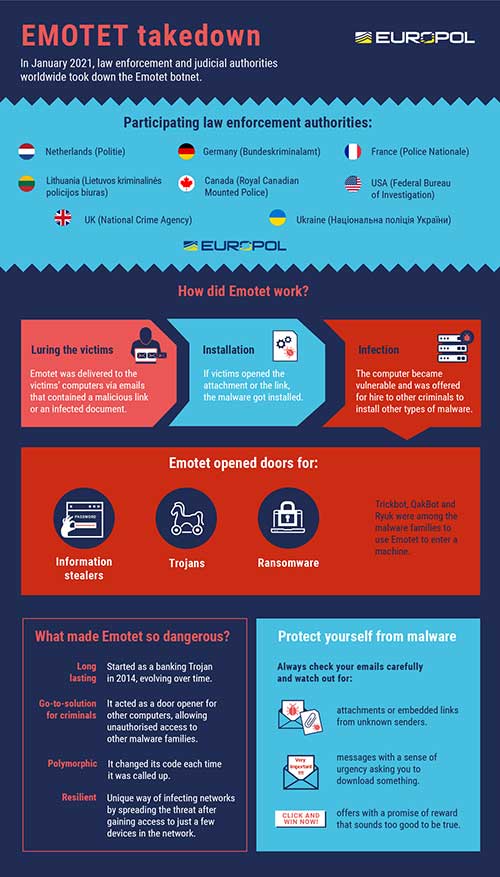
EMOTET has been one of the most professional and long-lasting cybercrime services out there. First discovered as a banking Trojan in 2014, the malware evolved into the go-to solution for cybercriminals over the years. The EMOTET infrastructure essentially acted as a primary door opener for computer systems on a global scale. Once this unauthorised access was established, these were sold to other top-level criminal groups to deploy further illicit activities such as data theft and extortion through ransomware.
The EMOTET group managed to take email as an attack vector to a next level. Through a fully automated process, EMOTET malware was delivered to the victims’ computers via infected email attachments. A variety of different lures were used to trick unsuspecting users into opening these malicious attachments. In the past, EMOTET email campaigns have also been presented as invoices, shipping notices and information about COVID-19.
All these emails contained malicious Word documents, either attached to the email itself or downloadable by clicking on a link within the email itself. Once a user opened one of these documents, they could be prompted to ‘enable macros’ so that the malicious code hidden in the Word file could run and install EMOTET malware on a victim’s computer.
Attacks for hire
EMOTET was much more than just a malware – what made EMOTET so dangerous is that the malware was offered for hire to other cybercriminals to install other types of malware, such as banking Trojans or ransomwares, onto a victim’s computer.
This type of attack is called a ‘loader’ operation and EMOTET is said to be one of the biggest players in the cybercrime world as other malware operators like TrickBot and Ryuk have benefitted from it.
Its unique way of infecting networks by spreading the threat laterally after gaining access to just a few devices in the network made it one of the most resilient malware in the wild.
Disruption of EMOTET’s infrastructure
The infrastructure that was used by EMOTET involved several hundreds of servers located across the world, all of these having different functionalities in order to manage the computers of the infected victims, to spread to new ones, to serve other criminal groups, and to ultimately make the network more resilient against takedown attempts.
To severely disrupt the EMOTET infrastructure, law enforcement teamed up to create an effective operational strategy. It resulted in the action whereby law enforcement and judicial authorities gained control of the infrastructure and took it down from the inside. The infected machines of victims have been redirected towards this law enforcement-controlled infrastructure. This is a unique and new approach to effectively disrupt the activities of the facilitators of cybercrime.
How to protect oneself against loaders
Many botnets like EMOTET are polymorphic in nature. This means that the malware changes its code each time it’s called up. Since many antivirus programmes scan the computer for known malware codes, a code change may cause difficulties for its detection, allowing the infection to go initially undetected.
A combination of both updated cybersecurity tools (antivirus and operating systems) and cybersecurity awareness is essential to avoid falling victim to sophisticated botnets like EMOTET. Users should carefully check their email and avoid opening messages and especially attachments from unknown senders. If a message seems too good to be true, it likely is and emails that implore a sense of urgency should be avoided at all costs.
Tom Bonner, Distinguished Threat Researcher, BlackBerry, commented on the incident: “The recent rise of the infamous Emotet malware attacks come as no surprise, as BlackBerry’s Threat Research and Intelligence team actively tracks the Emotet botnets Epoch 1, Epoch 2 and Epoch 3. This strain operates as a sophisticated malware delivery platform that is frequently updated to evolve and stay ahead of new security metrics and blockers built to fight it. As of late, the botnets we observed distributed banking trojans named Qbot and Trickbot, which were used to conduct a wide variety of criminal tactics, including credential stealing, Wi-Fi brute-forcing and spam distribution. They also ran network propagation modules that cyber-attackers can leverage to perform lateral movements once they hack into and have access within an organisation’s network post-infection.
“This strain of malware continues to be successful because Emotet has a good infrastructure for malicious activity. There are two things that make Emotet so stable: it is modularised to enhance its function, so consequently can conduct a wide-range of malicious activity based on the attacker’s command. Secondly, the developer of Emotet maintains the code well and it is continuously updated.”
Click below to share this article

