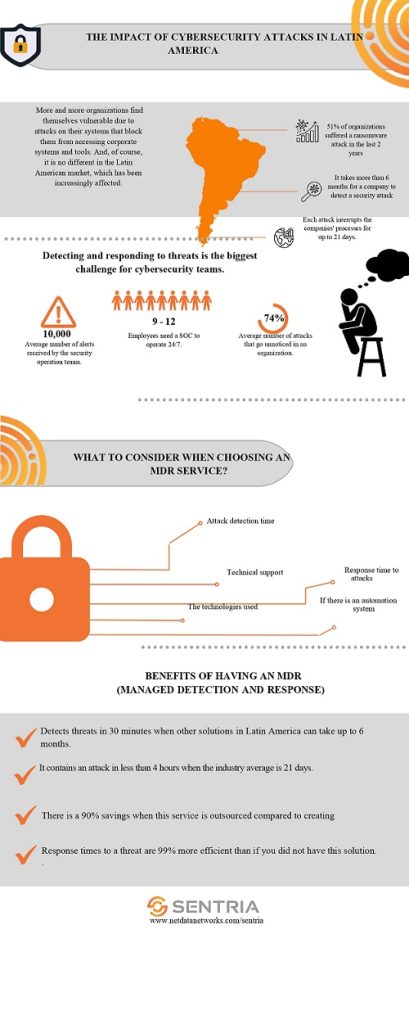
In recent years, more than 51% of companies in Latin America have suffered ransomware attacks. To address this scenario, Netdata explains how to deal with the impact of a cyberattack.
It is crucial that companies detect attacks before they become a real risk and before criminals turn business data into valuable assets.
According to Netdata figures, 51% of Latin American organizations have received a ransomware attack in the last two years because of the pandemic and digital acceleration, including the imposition of environments with weaker boundaries and less reliable connectivity.
It comprises everything from public network access to home services, among several other variables that have forced IT to sacrifice security to maintain productivity.
The landscape has changed somewhat during the second half of 2022.
However, according to Netdata, it can take up to six months for an organization to know it is under attack, and if successful, it can take up to 21 days to notice it.
Netdata also estimates that 74% of attacks go unnoticed by organizations.
How to respond?
For an attack, it is essential to remain vigilant. The proposal to implement a managed detection and response model, or MDR, is part of the alternatives currently considered to overcome threats.
The MDR model, such as Netdata’s Sentria, helps reduce the response time from weeks to minutes, containing an attack in about four hours instead of 21 days.
In terms of costs, they are reduced by 90% compared to renting a SOC. They are 99% more effective than having no functional solution.
Therefore, implementing an MDR may become a trend for Latin American companies for the remainder of this decade.
To prevent the attack from escalating, Netdata is looking for companies to find answers to the following issues:
- Forensic Investigation, with Sentria’s Cortex XDR Forensic Analysis module.
- Root Cause Hypothesis Analysis. According to the information given by the client, there will be some in-depth analysis that will help to better determine the causes of the problems and how to mitigate them.
- The use of UPSET Methodology to identify users, systems, persistence, TTP and the attacker’s target to perform determined actions.
- Identified IOC threat information.
- Determination of a possible timeline of the incident.
- Recommendations for actions to be taken.


