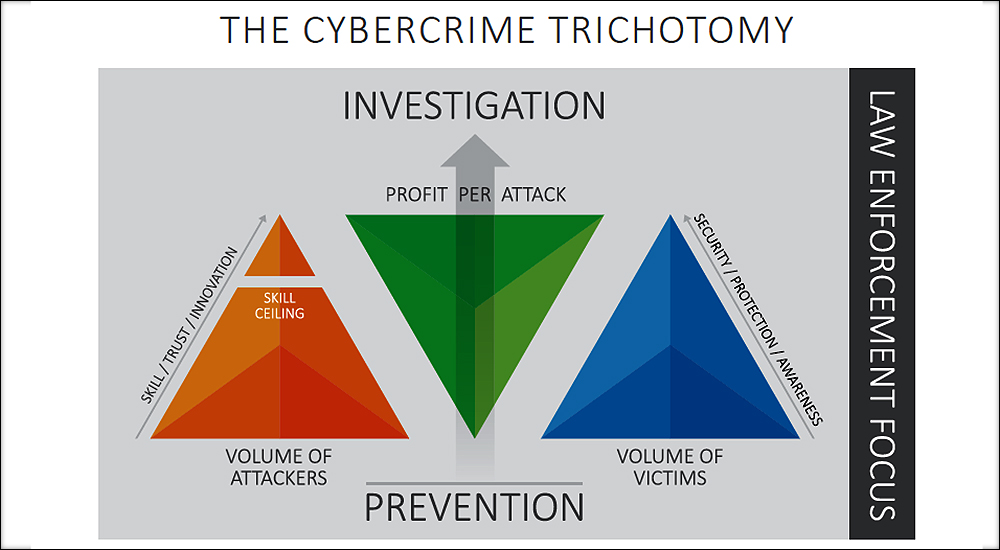
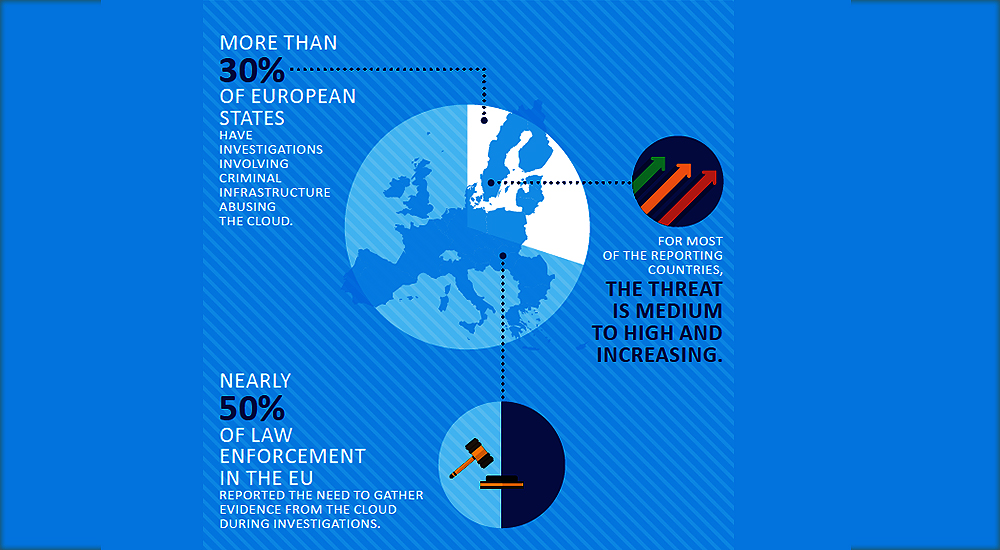
Poor digital hygiene enabling crime as a service, Europol 2016 report
Europol’s 2016 Internet Organised Crime Threat Assessment identifies an expanding cybercriminal economy exploiting increasingly Internet-enabled lives and low levels of digital hygiene. Informed largely by Europol’s law enforcement and cooperation partners, the report identifies eight main cybercrime trends and provides key recommendations to address the challenges.
The volume, scope and material cost of cybercrime all remain on an upward trend and have reached very high levels. Some EU Member States now report that the recording of cybercrime offences may have surpassed those associated with traditional crimes. An expansion both in the number of cybercriminal actors and opportunities to engage in highly profitable illegal activities has partly fueled this trend, as has the development of new cybercrime tools in areas such as ATM fraud and mobile malware.
However, a large part of the problem relates to poor digital security standards and practice by businesses and individuals. A significant proportion of cybercrime activity still involves the continuous recycling of relatively old techniques, security solutions for which are available but not widely adopted.
Europol’s Director Rob Wainwright: “The relentless growth of cybercrime remains a real and significant threat to our collective security in Europe. Europol is concerned about how an expanding cybercriminal community has been able to further exploit our increasing dependence on technology and the Internet. We have also seen a marked shift in cyber-facilitated activities relating to trafficking in human beings, terrorism and other threats.”
“In response law enforcement authorities have increased their skill-sets and their capability to work together in platforms such as the European Cybercrime Centre at Europol, but the growing misuse of legitimate anonymity and encryption services for illegal purposes remain a serious impediment to the detection, investigation and prosecution of criminals.”
The Head of the European Cybercrime Centre, Steven Wilson: “2016 has seen the further evolution of established cybercrime trends. The threat from ransomware has continued to grow and has now expanded into sectors such as healthcare. Europol has also seen the development of malware targeting the ATM network, impacting cash services worldwide. Online child sexual abuse continues to be a very high priority for all countries, with international cooperation established as a significant part of the strategy to protect children and identify victims.”
“However there are many positives to be taken from this year’s report. Partnerships between industry and law enforcement have improved significantly, leading to the disruption or arrest of many major cybercriminal syndicates and high-profile individuals associated with child abuse, cyber intrusions and payment card fraud, and to innovative new prevention programmes such as the no more ransom campaign.”
The eight cybercrime trends from Europol’s 2016 Internet Organised Crime Threat Assessment include:
#1 Crime-as-a-Service
The digital underground is underpinned by a growing Crime-as-a-Service model that interconnects specialist providers of cybercrime tools and services with an increasing number of organised crime groups. Terrorist actors clearly have the potential to access this sector in the future.
#2 Ransomware
Ransomware and banking Trojans remain the top malware threats, a trend unlikely to change for the foreseeable future.
#3 Criminal use of data
Data remains a key commodity for cyber-criminals. It is procured for immediate financial gain in many cases but, increasingly, also acquired to commit more complex fraud, encrypted for ransom, or used directly for extortion.
#4 Payment fraud
EMV chip and PIN, geo-blocking and other industry measures continue to erode card-present fraud within the EU, but logical and malware attacks directly against ATMs continue to evolve and proliferate. Organised crime groups are starting to manipulate or compromise payments involving contactless NFC cards.
#5 Online child sexual abuse
The use of end-to-end encrypted platforms for sharing media, coupled with the use of largely anonymous payment systems, has facilitated an escalation in the live streaming of child abuse.
#6 Abuse of the Darknet
The Darknet continues to enable criminals involved in a range of illicit activities, such as the exchange of child sexual exploitation material. The extent to which extremist groups currently use cyber techniques to conduct attacks are limited, but the availability of cybercrime tools and services, and illicit commodities such as firearms on the Darknet, provides opportunity for this to change.
#7 Social engineering
An increase of phishing aimed at high value targets has been registered by enforcement private sector authorities. CEO fraud, a refined variant of spear phishing, has become a key threat.
#8 Virtual currencies
Bitcoin remains the currency of choice for the payment for criminal products and services in the digital underground economy and the Darknet. Bitcoin has also become the standard payment solution for extortion payments.
Excerpts from the Executive Summary
Europol’s 2016 Internet Organised Crime Threat Assessment is produced by the European Cybercrime Centre EC3 at Europol. It informs decision-makers at strategic, policy and tactical levels in the fight against cybercrime, and focuses on three crime areas: cyber-attacks, online child sexual exploitation and payment fraud.
The 2016 Internet Organised Crime Threat Assessment reports a continuing and increasing acceleration of the security trends observed in previous assessments. The additional increase in volume, scope and financial damage combined with the asymmetric risk that characterises cybercrime has reached such a level that in some EU countries cybercrime may have surpassed traditional crime in terms of reporting. Some attacks, such as ransomware, which the previous report attributed to an increase in the aggressiveness of cybercrime, have become the norm, overshadowing traditional malware threats such as banking Trojans.
The mature Crime-as-a-Service model underpinning cybercrime continues to provide tools and services across the entire spectrum of cyber criminality, from entry-level to top-tier players, and any other seekers, including parties with other motivations such as terrorists. The boundaries between cybercriminals, Advanced Persistent Threat style actors, and other groups continue to blur. While the extent to which extremist groups currently use cyber techniques to conduct attacks appears to be limited, the availability of cybercrime tools and services, and illicit commodities such as firearms on the Darknet, provide ample opportunities for this situation to change.
Many of the key threats remain largely unchanged from the previous report. Ransomware and banking Trojans remain top malware threats – a trend unlikely to change for the foreseeable future. While the same data stealing malware largely appears year-on-year, ransomware, a comparatively more recent threat is in greater flux and may take several more years before it reaches the same level of equilibrium.
Peer-to-peer networks and the growing number of forums on the Darknet continue to facilitate the exchange of child sexual exploitation material, while both self-generated indecent material and content derived from the growing phenomenon of live-distant child abuse, further contribute to the volume of child sexual exploitation material available.
EMV chip and PIN, geoblocking and other industry measures continue to erode card-present fraud within the EU, forcing criminals to migrate cash out operations to other regions. Logical and malware attacks directly against ATMs continue to evolve and proliferate. The proportion of card fraud attributed to card-not-present transactions continues to grow, with e-commerce, airline tickets, car rentals and accommodation representing the industries hit hardest. The first indications that organised crime groups are starting to manipulate or compromise payments involving contactless cards have also been seen.
The overall quality and authenticity of phishing campaigns has increased, with targeted spear phishing aimed at high value targets, including CEO fraud, reported as a key threat by law enforcement and the private sector alike.
DDoS attacks continue to grow in intensity and complexity, with many attacks blending network and application layer attacks. Booters, stressers are readily available as-a-service, accounting for an increasing number of DDoS attacks. While other network attacks aimed at exfiltrating data continue to focus on financial credentials, there is a growing trend in the compromise of other data types, such as medical or other sensitive data or intellectual property for other purposes.
Cryptocurrencies, specifically Bitcoin, remain the currency of choice for much of cybercrime, whether it is used as payment for criminal services or for receiving payments from extortion victims. Even so, key members of the Bitcoin community, such as exchangers, are increasingly finding themselves the victim of cybercriminals.
The growing misuse of legitimate anonymity and encryption services and tools for illegal purposes poses a serious impediment to detection, investigation and prosecution, thereby creating a high level of threat cutting across all crime areas. For law enforcement in particular, this creates a dichotomy of value. Strong encryption is highly important to e-commerce and other cyberspace activity, but adequate security depends on police having the ability to investigate criminal activity.
It should be noted that the majority of reported attacks are neither sophisticated nor advanced. While it is true that in some areas cybercriminals demonstrate a high degree of sophistication in the tools, tactics and processes they employ, many forms of attack work because of a lack of digital hygiene, a lack of security by design and a lack of user awareness.
Nevertheless, a variety of new and innovative modi operandi have been discovered, combining existing approaches, exploiting new technology or identifying new targets. The proliferation and evolution of malware attacks directly against ATMs, indications of compromised payments involving contactless cards and the recent attacks against the SWIFT system are examples of this development.
The networking model employed by Europol’s EC3 continues to provide tangible results in the fight against cybercrime at EU level and beyond. In the last year the number of successful high-level operations supported by the EC3, rose from 72 operations during 2014, to 131 in 2015.
However, law enforcement, policy makers, legislators, academia and training providers need to become even more adaptive and agile in addressing the phenomenon. Existing frameworks, programmes and tools are often too slow and bureaucratic to allow for a timely and effective response. Rather than multiple partners investing in and developing the same highly specialised skillsets and expertise, perhaps a more effective, high-level model would be for law enforcement and relevant partners to focus on distinct core competencies and to make them available to others as a service.
It is important to consider law enforcement as one of the key partners in ensuring cybersecurity in the EU.
Signup to the Intelligent CIO Africa newsletter and never miss out on the latest news