Dr. Renée Burton, Senior Director of Threat Intelligence for Infoblox, tells us how the rising prevalence of multi-factor authentication (MFA) has made it a target for cybercriminals, and discusses Infoblox’s strategies to counter these evolving threats.

Over the last several years, the adoption of multi-factor authentication (MFA) has gained momentum. Consumer advocates and government agencies alike recommend that everyone adopt the technology. As is often the case, when something becomes popular, it becomes a target; MFA is no different. Years ago, security campaigns encouraged users to move from easily-guessed passwords to stronger passwords containing a variety of characters. In doing so, individuals and enterprises gained a sense of confidence from adopting another defense against criminals lurking on the internet.
But criminals are both persistent and smart: as people got tired of remembering all their now-complex passwords, they started storing them in password “wallets,” which the bad actors then targeted. Essentially, the same has happened with MFA. Multi-factor authentication, also known as two-factor authentication (2FA), adds additional security to online accounts and systems by requiring a user to verify their login request with something beyond their password. As users have become more confident in and reliant on MFA preventing compromise, threat actors began targeting MFA services as they were commercialized into a fairly small number of brokers. In defense, we are introducing a new algorithm class in Threat Insight called Rapid Domain Triage. With this capability, BloxOne Threat Defense customers will be able to automatically block suspicious domains in near real-time and be alerted of activity that will allow them to remediate attacks more quickly.
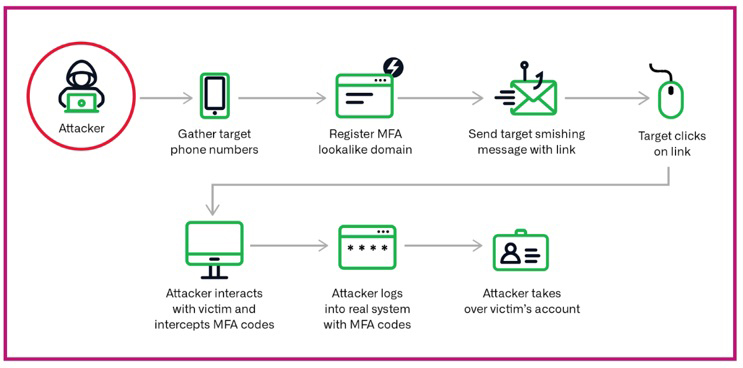
As Infoblox and others have reported, fake MFA domain attacks have risen greatly in the last 15 months, aided by a cheap toolkit available on the dark market to quickly implement an adversary-in-the-middle (AiTM) attack at scale.1 While the specifics vary, a common MFA attack works like this:
- the attacker obtains a set of phone numbers of their targets
- they register a domain name that is a lookalike to MFA, 2FA, Okta, Duo, or one of a handful other well-known verification keywords
- they use a toolkit to send out SMS text messages with some kind of urgent message requesting the user to verify their credentials to an account
- when the user clicks on the link, the attacker actively interacts with them and intercepts the MFA codes; they may even phone the victim to further the deception
- the attacker relays the user’s MFA codes into the real system and gains access to user’s account
- from there, the actors may perform other attacks to gain further access and escalate their privileges, or they may just steal user information and move on
These phishing attacks are used against consumers and enterprises alike. Infoblox has custom algorithms designed to detect the registration and utilization of MFA-lookalike domains, and we observe both widespread targeting of banking and other financial services, as well as spear phishing of institutions. We have seen a consistent rise in these attacks since June 2022 and detect hundreds of new MFA-lookalike domains every month. Mandiant recently reported that MFA SMS phishing (smishing) is a favorite technique of Scatter Spider, the actor behind the disruption of both MGM International and Caesars networks in September 2023.
We detect dozens of these domains queried in customer networks every month. While that may not seem like many, it only takes one successful phish to compromise a network. Software company Retool disclosed that this exact scenario happened to them in late-August 2023, impacting nearly 30 of their cloud customers. Like Coinbase had done earlier this year, Retool provided a detailed account of the hack. In the Retool case, a Google setting, designed as a convenience feature for users, allowed the attacker much more significant access to internal networks than they would have gained from a standard AiTM smishing attack. Retool rightfully pointed out that in this case, MFA was no longer MFA because access to a single user’s google account gave them access to all of that user’s internal applications. The hackers had both successfully targeted the company’s MFA authentication and Google’s MFA synchronization.
The details that Retool provided allowed us to take a closer look at the attack and compare its domains with others we have detected recently as MFA phishing. Retool fell victim to a spear smishing attack on August 27th. A number of their employees received SMS messages indicating a problem that might prohibit their ability to enroll in healthcare coverage and including a link that appeared to be an Okta login. While most recipients disregarded the text messages, one employee followed the link. In this case, the attacker immediately phoned the employee pretending to be a member of their IT department. This extra step helped cement employee trust; when the employee provided their MFA credentials, the attacker gained access to their corporate Google account. Unfortunately, they also were able to retrieve the user’s MFA tokens for other applications and penetrate internal networks. As Retool explains, this attack was not the fault of the employee. Hackers like this are con artists, and con artists are successful because they are good at social engineering, not because their victims are stupid. The scenario Retool faced has increasingly been observed over the last 15-18 months, although it was exacerbated by a GSuite setting that synchronized all of their active tokens into the cloud.
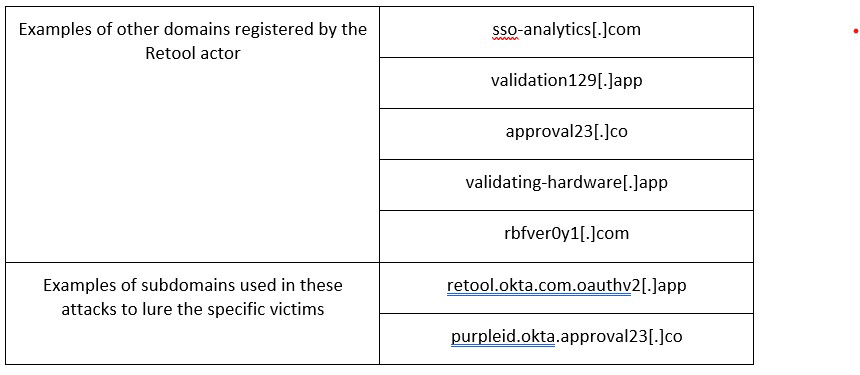
The link that the Retool employee clicked on was this: https://retool[.]okta[.]com[.]oauthv2[.]app/authorize-client/xxx
The second level domain, oauthv2[.]app, was registered the same day it was used against Retool, August 27th. We have found that almost 100% of MFA-lookalike domains are used by the actor within 24 hours of registration. This is in startling contrast to the bulk of phishing domains we observe, where only 55% of them were used the same day they were registered. Many years ago, phishing domains were registered and used immediately, then dropped nearly as quickly, in a rapid cycle. However, the security industry was quick to develop a response to these tactics including the blocking of newly registered domains and the development of scanning systems that looked for active phishing content based on registration data. Phishers responded by delaying the use of their domains, a practice called strategic aging. Our data over the last 5 years has consistently shown a trend in phishing toward strategic aging, with over 30% of domains being first observed in campaigns more than 3 days after registration.
If phishers wait to use their domains, why do those using MFA-lookalikes use them in campaigns immediately? We don’t know for sure, but we suspect it is an attempt to catch security systems unprepared. Unlike common phishing attacks, Retool employees were targeted using specific information about their company healthcare enrollment; this is called spearphishing. In these highly focused attacks, the actor typically creates a domain name that combines terms that reference multifactor authentication, such as 2FA, Okta, MFA or verify; with the company name. In the Retool attack, the domain oauthv2[.]com looks like a verification domain, but the actor added both retool and okta into the subdomains to further their deception. However, this kind of domain is likely to be picked up by domain name-based detection systems like ours. Indeed, it was. By acting quickly, the actor took advantage of the delay in security systems.
While there is no evidence that the domain oauthv2[.]com was used to target other companies, they could easily do so with a structure similar to the one used in the attack. We can see from global passive DNS (pDNS) data that the same actor registered a number of MFA lookalike domains around the same time. They appear to be targeting both general consumers and specific enterprises, based on the breadth of subdomains we observed in pDNS, as well as the other domains they have registered. Several of the subdomains suggest Coinbase, FedEx, ShipBob, Cox Communications have been targeted, among others.
We detected a likely different actor conducting similar operations in September. The domains com-2fa[.]support, com-2fa[.].help, reset-2fa[.]com, and com-reset[.]help included Coinbase in the subdomains, e.g., coinbase.com-2fa[.]support. Based on our MFA lookalike detections over the past 6 months, Coinbase may be the most targeted of all companies for recent MFA spear phishing attacks, with a fairly constant set of domains designed to fool their customers or employees. Similar to the Retool attacker, this actor runs a range of phishing attacks including lookalikes to various cryptocurrency sites.2
While generic MFA lookalikes are common, we also detect a large number of malicious domains that include both a company lookalike and a term associated with MFA. Often the company name will be shortened or misspelled. Financial institutions and internet service providers are common targets of this approach. Examples of such phishing domains observed in September include samtanfe-verify[.]click, 2fa-portal-nsandi[.]com, scotiasecureinfo-verify[.]services, and verify-wick[.]xyz. These domains are lookalikes to entities in banking and Discord bots. While we detect hundreds of MFA lookalikes every month, we detect tens of thousands of lookalikes to commercial enterprises and services. Frequently threat actors, like the one that attacked Retool, will dabble in a variety of methods to exploit users, including general lookalike phishing domains as well as spear phishing. The actor who registered com-2fa[.]support, for example, also registered coinbase-live[.]support and smart-core[.]fr, both lookalikes to cryptocurrency companies.
The sheer number of lookalike domains we detect demonstrates the burden on users to guard both their home and their workplace. While some security pundits argue that successful attacks highlight the need for more vigilance on the part of users, shaming users for the failure of security systems to protect them is not the answer. Infoblox has had lookalike detection in place for three years, and specially tuned MFA-lookalike detection since early this year, in order to find and block the domains before they impact our customers. We are constantly refining our approach and learning from events where we failed to detect malicious activity.
Although the Retool compromise came via an SMS message, MFA lookalike attacks are delivered other ways as well. Phishing emails, compromised and fraudulent websites, and malvertising are all some ways that an attacker can deliver a link. Earlier this year, the US Cybersecurity and Infrastructure Security (CISA) released a joint Cybersecurity Advisory regarding a phishing campaign that involves the malicious use of legitimate remote monitoring and management (RMM) software.3 In those incidents, the attacker prompted the user to enter a lookalike domain over the phone into a web browser. There are many ways to trick a user to visit a domain!
Whether you are receiving a prompt for MFA as a consumer or an employee, be skeptical if there is anything unusual about it. Criminals have all day to think about new ways to fool you and so it is important to be ever vigilant. At the same time, we in the security industry shouldn’t participate in victim blaming. It is our job to constantly improve our abilities to automatically thwart the bad guys and try to turn the tables on them. With MFA lookalikes and the broad push to adopt the technology, we’ve also given them a way to focus their attention.
We became alarmed by the use of MFA-lookalike domains immediately following their registration for spear phishing attacks early this year. While these attacks are rare, when successful they can be profoundly damaging, as the Retool hack attests. We became aware of multiple instances where we flagged a domain as suspicious a few hours after the attack, including the domain used against Retool. Luckily, Infoblox‘s BloxOne Threat Defense includes a key module called Threat Insight, which has been detecting Data Exfiltration and Domain Generation Algorithm (DGA) threats in near-real time since 2015, providing our customers with threat detection tailored specifically to their network.
Retool’s attacker was able to use the stolen MFA tokens to access several internal systems and take over 27 customer accounts. All of this took some time, both for the attacker to accomplish and for Retool to discover. With Rapid Domain Triage, Retool would have received an alert for a potential spear phishing attack on their network with all the asset and timing information necessary for them to isolate the device and perhaps even thwart the attacker before they were fully inside their systems.
Click below to share this article

